Phishing Information and Awareness
What is Phishing?
"Phishing" messages are fraudulent e-mails sent by criminals (such as identity thieves and hackers) that try to trick recipients into doing their bidding. The motives behind phishing are myriad, but common objectives include:
- Getting sensitive personal information from victims (such as Social Security numbers, dates of birth, and credit card information)
- Stealing usernames and passwords for use in cyberattacks against UWGB or other organizations
Sending victims to a website which will attempt to install malware on their computer
To this end, they are designed to mimic genuine e-mails from real organizations in order to create trust. However, many phishing e-mails contain "tells" that can help users identify and steer clear of them.
How to Identify Phishing
Phishing e-mails often possess certain traits that give away their true purpose. Here are some common signs that an e-mail may be a phishing attempt:
Requests to send personal information via e-mail
- Neither UW-Green Bay nor any other reputable organization should ever ask you to furnish sensitive information (such as your password or Social Security number) by e-mail.
- If ever in doubt, contact the purported sender by phone or in person. They should be able to verify for you whether or not the message you received is legitimate.
A scammer might ask you for information like your full name, contact address, phone number, age, or more.
Unreasonable urgency or use of fear tactics
- Phishing e-mails will often feign urgency or use fear tactics in order to rush readers into making a rash decision. For instance, they may threaten that your e-mail account will be deleted unless you "verify your account details" within a short period of time, or claim that you have been "hacked" and that you must quickly run an attached program to save your files.

If you encounter such an e-mail and are worried about whether or not it is legitimate, feel free to send the suspect message to abuse@uwgb.edu or call the IT Service Desk at 920-465-2309 for our opinion.
Uncharacteristic errors or unprofessionalism
- Large organizations generally have the time and resources to make the e-mails they send look and feel professional. Phishers, on the other hand, may not. Accordingly, phishing e-mails often contain:
- Unusual errors in spelling and grammar:

- Stretched, low-resolution, or outdated logos
- None of the legal fine print (e.g. copyright notices) that usually accompanies legitimate e-mails from businesses
- Unusual errors in spelling and grammar:
- For instance, if an e-mail claims to be from Facebook but is riddled with spelling mistakes, it's probably fraudulent.
However, be careful not to let your guard down just because the message looks right. Some phishers have grown quite adept at imitating those organizations that they impersonate.
Invitations or attachments you weren't expecting
- Many phishing scams involve distributing fake invitations or malicious attachments. Spearphishers (phishers who target individual people) may imitate someone you know in order to make this sort of scam appear more trustworthy. Therefore, even if they look like they came from someone you trust, be wary of invitations or attachments unless you were already expecting them. If in doubt, you can always ask the purported sender in person or by phone to find out whether it really came from them.
- One particularly popular variant of this attack involves trying to trick recipients into opening a malicious file by hiding it behind a service like Google Drive, Office 365, or Dropbox. Because these invitation e-mails are usually sent from an address belonging to the file sharing service rather than the person offering the invitation, this tactic allows phishers to skirt spam filters and leverage the trust that users place in these legitimate, widely-used products. Keep a close eye out for these.
Finally, remember that, as the old adage goes, "If it's too good to be true, it usually is."

How to Avoid Phishing
Here are some actions that students, faculty, and staff can take to protect themselves against phishing:
Verify links by hovering or long-pressing - look before you leap!
- By hovering your cursor over a link or button before you click it, you can check where it's actually going to take you.
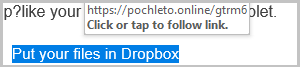
- If you're using a touchscreen device such as a smartphone or tablet, you can usually find out where a link is going to take you by "long pressing" it - that is, pressing and holding it for a couple of seconds. This should open a window which shows where the link leads and provides several actions you can take with it. If you do not wish to visit the link in question, you can then close this window by tapping outside of its bounds or, if applicable, pressing the "Back" button.
Be careful: Links to URL shortening services such as bit.ly are often used to conceal what would otherwise be suspicious destinations. If in doubt, don't click it!
Don't use your UW-Green Bay e-mail for personal business
The advantage: Know immediately that e-mails which reference personal matters like your bank or Facebook account are phony!
Trust, but verify - don't be afraid to pick up the phone!
If you receive a suspicious-looking e-mail from a fellow student or coworker, it may be that they're being impersonated or that their e-mail account or computer has been compromised by a phisher. If in doubt, ask them by phone or in person whether the message they supposedly sent is legitimate or not.
Practice makes perfect
Try SonicWall's Phishing IQ test to hone your phishing identification skills!
How to Report Phishing
Found an e-mail that looks suspicious? Phish Wanted! Please forward the email as an attachment to abuse@uwgb.edu.
Click here for a Phish wanted poster that you can print and keep near your workstation as a handy reminder of what to look out for in a suspicious email.